Digital Certificate
What is a Digital Certificate?
In simple terms, a Digital Certificate or Digital ID as it is sometimes known, is the electronic commerce world's analogue of the passport. It is a credential issued by a trusted authority that binds you as an individual to an identity that can be recognised and verified electronically by other agencies. It confers certain rights and obligations on you according to policies exercised by the Issuing Authority. Because it uses cryptographic technology, it provides you with the ability to digitally sign emails, documents or transactions, or to verify the signatures of others. It enables you to make emails, documents or transactions only readable by those that you designate.
In a real passport, various checks on you are made by a trusted representative of the Issuing Authority to ensure that you are who you say you are, and thus establish a binding between you as an individual and the paper document that declares your identity. In the digital certificate world, a trusted representative of the Issuing Authority must be satisfied that you are who you say you are, before a request is made to issue a digital certificate on your behalf. Just as when a government issues you with a passport, it is officially vouching for the fact that you are who you say you are, when a Digital Certificate Issuing Authority gives you a digital certificate for secure email, it is putting its name behind the claim that you are the holder of your e-mail address.
In a real passport, the methods used to ensure the integrity of the binding between you and the paper identity are such things as watermarks, seals, special paper and ink, etc. In the digital certificate world, the method used to ensure the integrity of the binding between an individual or other entity and the public key, is the digital signature of the Issuing Authority.
What is a Root Certificate?
A root certificate is the digital certificate of an Issuing Authority. The public key in this certificate is used to verify the digital signature of the Issuing Authority. The Issuing Authority's digital signature is present in all certificates that it issues. The root certificate therefore, can be used to verify the integrity of any certificate that was issued by it. By downloading the root certificate, the user indicates trust in the Issuing Authority, and therefore trust in the bindings that it creates between real identities and their digital certificates.
How do Digital Certificates Work?
One widely-used tool for privacy protection is what cryptographers call "symmetric" or "secret key" encryption, called that way because one encryption key is used to both encrypt and to decrypt information. This key should obviously be kept secret from anyone not authorised to decrypt the information. Your log-on password, your cash card PIN, and the information you type in to enter your online bank accounts are all examples of secret keys. You share these secret keys only with the parties you want to communicate with, such as the bank or credit card company. Your private information is then encrypted with this secret key, and it can only be decrypted by one of the parties holding that same key.
Despite its widespread use, this secret-key system has some serious limitations. As network communications proliferate, it becomes very cumbersome for users to create and remember different passwords for each situation. Moreover, the sharing of a secret key involves inherent risks. When you give your mother's maiden name over the telephone, how do you know you can trust the party on the other end of the line? Can you be sure it is really the credit card company you are talking to? Can you be sure nobody is maliciously listening in? If you give somebody your mother's maiden name and that person abuses it for their own gain, how can you prove you did not authorise their use?
Digital Certificate technology addresses these issues because it does not rely on the sharing of secret keys. Rather than using the same key to both encrypt and decrypt data, a Digital Certificate uses a matched pair of keys which complement one another. In other words, what is done by one key can only be undone by the other key in the pair. In this type of key-pair system, a user holds onto a "private key" and never gives it to anyone, while widely disseminating a "public key." Any information locked with the public key can only be unlocked by the corresponding private key, and vice versa. Since the public key alone does not provide access to communications, users do not need to worry about who gets hold of this key.
For example, for the purposes of securing e-mail, key pairs can work in the following two ways.
You can digitally sign your e-mail by enclosing an electronic stamp constructed by using your private key. When your recipient gets your message, their computer checks this stamp to see if it can be decrypted using your public key. If successful, the recipient knows that the message can only have come from the holder of the private key.
Someone who wants to send you private e-mail can use your public key to encrypt the message. When you get the e-mail, your computer checks to see if the public key used to encrypt the e-mail is a valid match with your private key. If the match is successful, the message gets decrypted and you can read it. Anyone who receives your e-mail but does not hold your private key will be unable to decrypt and read the message.
.
A Digital Certificate makes it possible to verify someone's claim that they are the rightful owner of a given key, helping to prevent people from using counterfeit or stolen keys to impersonate other users. Used in conjunction with encryption, Digital Certificates provide a more complete security solution, assuring the identity of all parties involved in a transaction.
Because a Digital Certificate uses and supplies us with the tools of cryptographic technology, it provides us with the ability to digitally sign documents or transactions, or to verify the signatures of others. It enables us to make documents or transactions only readable by those that we designate. Because Digital Certificates bind a public key to an individual or organisation, in a trusted manner, we can be sure of the identities behind these operations.
Who needs a Digital Certificate?
Anyone who wants to receive encrypted e-mail so they know nobody else can read it will need a Digital Certificate. Anyone who wants to digitally sign their e-mail so that recipients can feel confident it came from them will also need a Digital Certificate.
How do I get a Digital Certificate?
Your organisation has identified one or more responsible and trusted individuals who will act in the role of Registration Authority. It is their job to ensure that everyone who holds a certificate is in fact eligible to do so, that they are who they say they are, and that all details recorded on the certificate about the holder are accurate. Your Registration Authority is where you need to apply for a certificate. You should also contact them immediately if you suspect that your private key has been compromised or stolen, or if any details about you have changed (email address, name, etc.).
Who manages my organisation's Digital Certificates?
Your organisation has identified one or more responsible and trusted individuals who will act in the role of Registration Authority. It is their job to ensure that everyone who holds a certificate is in fact eligible to do so, that they are who they say they are, and that all details recorded on the certificate about the holder are accurate. Your Registration Authority is where you need to apply for a certificate
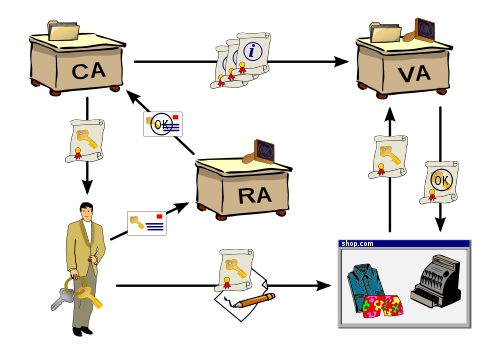 Public Key Infrastructure or PKI can be a very complex but important subject. We’ll give you a PKI overview to help you understand what PKI is and how it can help you. PKI is a loaded term that involves the hardware, software, policies, and standards that are necessary to manage SSL certificates. A PKI lets you:
Public Key Infrastructure or PKI can be a very complex but important subject. We’ll give you a PKI overview to help you understand what PKI is and how it can help you. PKI is a loaded term that involves the hardware, software, policies, and standards that are necessary to manage SSL certificates. A PKI lets you: